The National Vulnerability Database (NVD), a US government repository of standards-based vulnerability data that enables organizations and cybersecurity solutions to detect and manage vulnerabilities to protect against cyberattacks, hasn’t been updated for several weeks. This means that important data is missing for more than 2,000 of the most recent vulnerabilities, including some that are being actively exploited.
According to their website: “NIST is currently working to establish a consortium to address challenges in the NVD program and develop improved tools and methods. You will temporarily see delays in analysis efforts during this transition. We apologize for the inconvenience and ask for your patience as we work to improve the NVD program.”
Given the centrality of NVD to the overall process of assessing and identifying vulnerabilities, this is a concerning development. Therefore, we recommend that organizations ensure they are not relying heavily on only NVD data for their vulnerability management and check that their cybersecurity vendors are also pulling vulnerability data from several other reputable sources rather than relying on NVD data alone.
We want to inform Orca customers that the NVD delays do not affect Orca’s ability to detect and alert on existing and new CVEs. The Orca Platform utilizes more than 20 vulnerability sources, and does not solely rely on NVD for Common Platform Enumerations (CPEs) and Common Vulnerability Scoring System (CVSS) scores. Orca will continue to monitor the situation as it unfolds and provide updates as new information emerges.
What is NVD?
The National Vulnerability Database (NVD) has been active since 1999 as a clearinghouse for information on reported vulnerabilities, or CVEs. NVD has a page for every reported CVE and, importantly, augments each report with a score indicating how severe the vulnerability is and why (CVSS) and information about which versions of which libraries are affected (CPE).
NVD enriches the vulnerability data with the following information:
- Vulnerability descriptions: Detailed descriptions of vulnerabilities, including their severity, affected products, and potential impact.
- Common Vulnerability Scoring System (CVSS): The NVD assigns CVSS scores to vulnerabilities, providing a standardized way to assess their severity and prioritize remediation efforts.
- Remediation information: Guidance on how to mitigate vulnerabilities, including patches, workarounds, and best practices for securing systems.
- Metrics and trends: Analysis of vulnerability data, including trends over time, common types of vulnerabilities, and emerging threats.
The NVD offers data feeds and APIs for automated access to vulnerability information, enabling integration with cybersecurity tools and platforms.
Are Orca Security customers impacted?
The Orca Cloud Security Platform does not depend on NVD for Common Platform Enumerations (CPEs) and CVSS scores, instead primarily using a variety of sources including OS vendors, GitHub Advisories (GHSA), and data from other sources and only using NVD to augment that data. The missing NVD data will not affect the Orca Platform’s ability to detect and alert on existing and new CVEs. It may have a minor impact on a small number of dashboard widgets or queries that rely specifically on the NVD CVSS score or derived severity, with more items than expected being categorized as ‘Other’ in graphs and tables.
How does Orca perform vulnerability management?
Orca performs agentless scanning of AWS, Azure, Google Cloud, Kubernetes and more, to create a full inventory of the cloud environment and leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate.
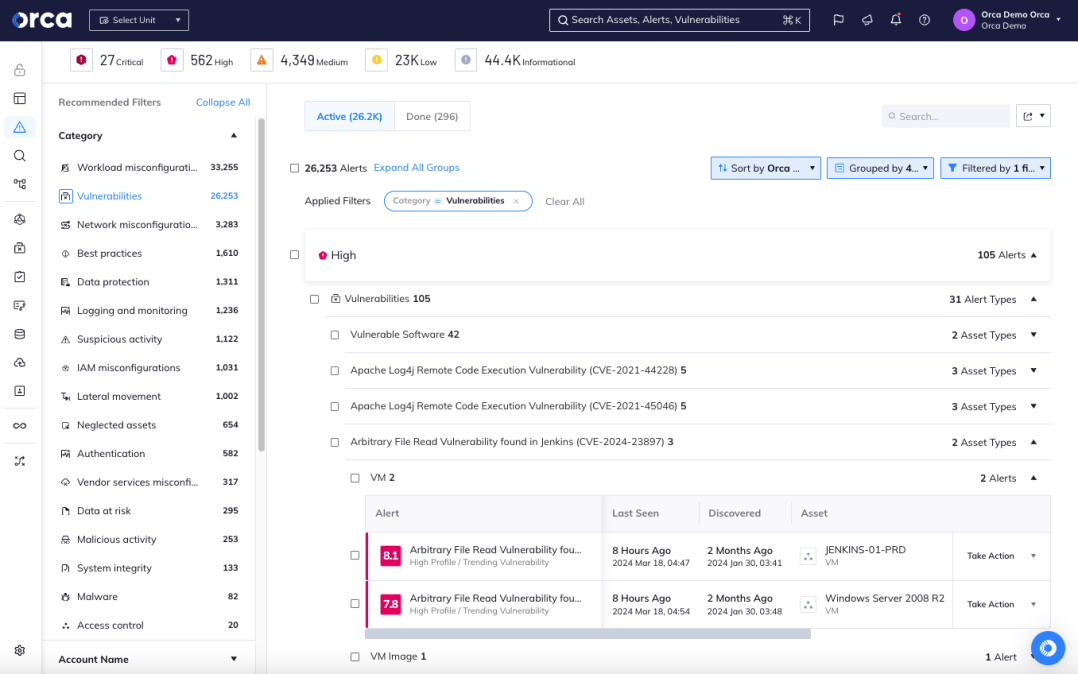
The Orca Platform detects and scores all vulnerabilities found in the cloud environment
Orca covers OS packages, applications, and libraries and alerts on any vulnerabilities found. Unlike other solutions that simply report on the CVSS score, Orca considers the context of cloud assets, their connections and risks, and applies a granular risk score, so security teams understand which vulnerabilities are the most critical and need to be addressed first.
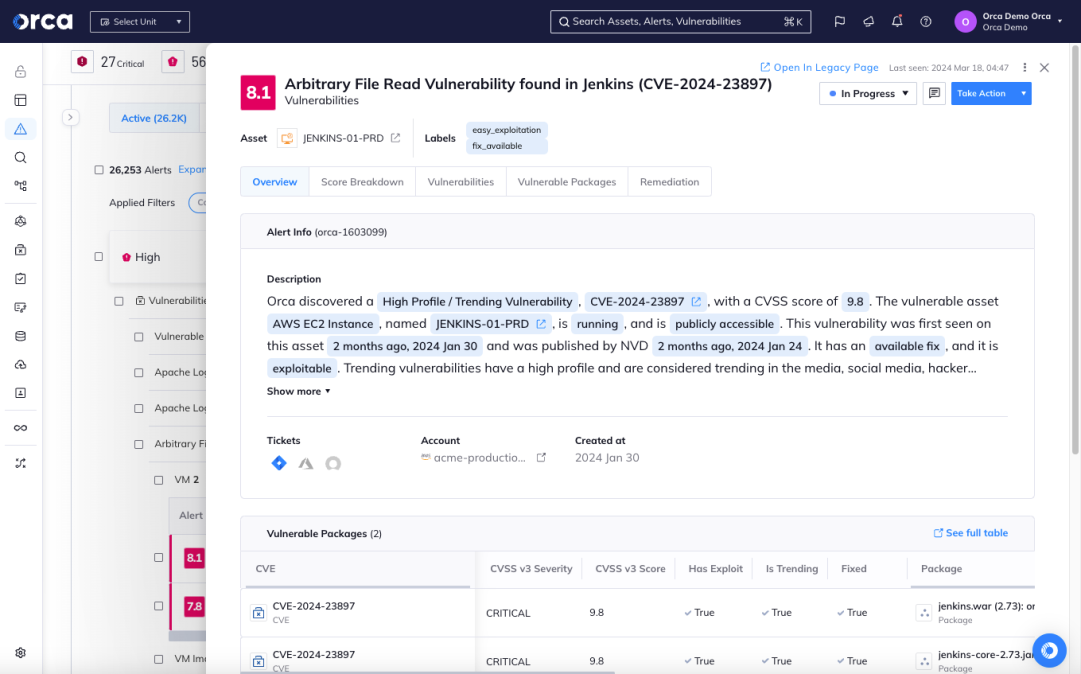
Orca has scored this vulnerability as 8.1 and provides a detailed explanation in the description
In addition to vulnerability management, Orca provides comprehensive cloud security across every layer of the cloud estate, detecting malware, misconfigurations, overly privileged identities, API risk, sensitive data at risk, lateral movement risk, and suspicious activity.




